 Zong Wins Fastest Growing Network Award
Zong Wins Fastest Growing Network Award
Mr. Fan Yunjun, CEO, Zong, accepting ‘Fastest Growing Cellular Network Award’ from Mr. Mamnoon Hussain, President of Pakistan, at RCCI...
 Zong Wins Fastest Growing Network Award
Zong Wins Fastest Growing Network Award
Mr. Fan Yunjun, CEO, Zong, accepting ‘Fastest Growing Cellular Network Award’ from Mr. Mamnoon Hussain, President of Pakistan, at RCCI...
 Warid Introduces Back to Fun offer
Warid Introduces Back to Fun offer
Glow by Warid is offering its subscribers 10,000 free minutes, SMS, and MBs mobile internet. Those Glow customers who have not used thei...
 Mobilink Foundation Support the Residents of Dar-ul-Sukun
Mobilink Foundation Support the Residents of Dar-ul-Sukun
Mobilink Foundation Torchbearers (employee volunteers) extended their support to residents of Dar-ul-Sukun, Karachi as a means of a...
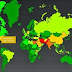 Pakistan, Among Top 5 NSA Targets, Takes Steps to Secure its Cyber Space
Pakistan, Among Top 5 NSA Targets, Takes Steps to Secure its Cyber Space
NSA’s color-coded global heat maps, — a pictographic portrayal of the extent of its surveillance around the world, ranging from green,...
 Ufone Launches Industry’s First Website Builder
Ufone Launches Industry’s First Website Builder
While staying abreast with the market needs, Ufone has now initiated a website generating amenity called the Ufone Business Website serv...
 IT Companies to Represent Pakistan at GITEX 2013
IT Companies to Represent Pakistan at GITEX 2013
14 IT companies are planning to participate at Middle East Africa and South Asia’s (MEASA) top ICT event GITEX Technology Week 2013, whi...